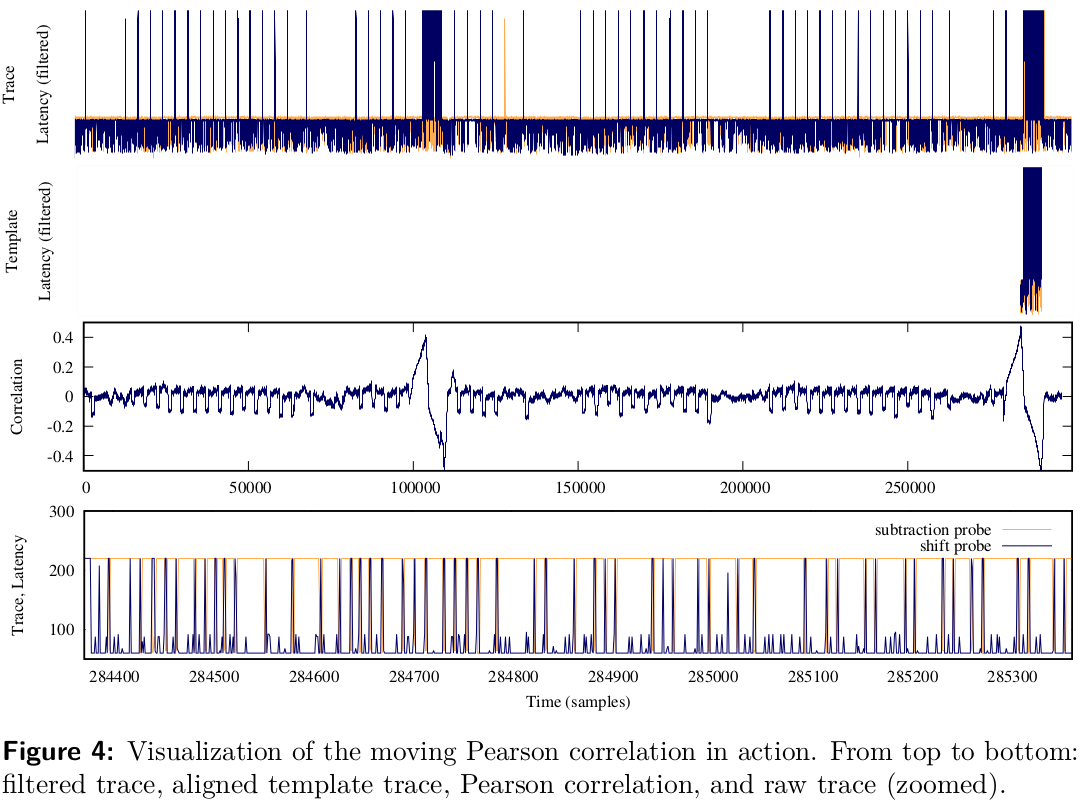
Title: Cache-Timing Attacks on RSA Key Generation
Authors: Alejandro Cabrera Aldaya and Cesar Pereida García and Luis Manuel Alvarez Tapia and Billy Bob Brumley
Venue: Cryptographic Hardware and Embedded Systems, CHES 2019, Atlanta, GA, USA, August 25-28, 2019
Congrats to @acaldaya @lalvarezt89 and NISEC's @CesarPereidaG: "Cache-Timing Attacks on RSA Key Generation" to appear @2019ches Conference on Cryptographic Hardware and Embedded Systems in Aug. Updated #ePrint https://t.co/CVK1FpEjco #OpenSSL CVE-2018-0737 #sidechannel #infosec pic.twitter.com/QzvNvDJi6a
— NISEC (@NISEC_TAU) July 8, 2019
Implementing gcd/xgcd/modinv? Heard about Microsoft SymCrypt gcd running forever (https://t.co/8GnlJ9qKk9) and OpenSSL gcd leaking secret keys via timing (https://t.co/7HadxKXSqO)? Bo-Yin Yang and I have a paper https://t.co/vTuAdTUSJP with a simple constant-time gcd algorithm.
— Daniel J. Bernstein (@hashbreaker) June 13, 2019
https://twitter.com/CesarPereidaG/status/988874867671031815