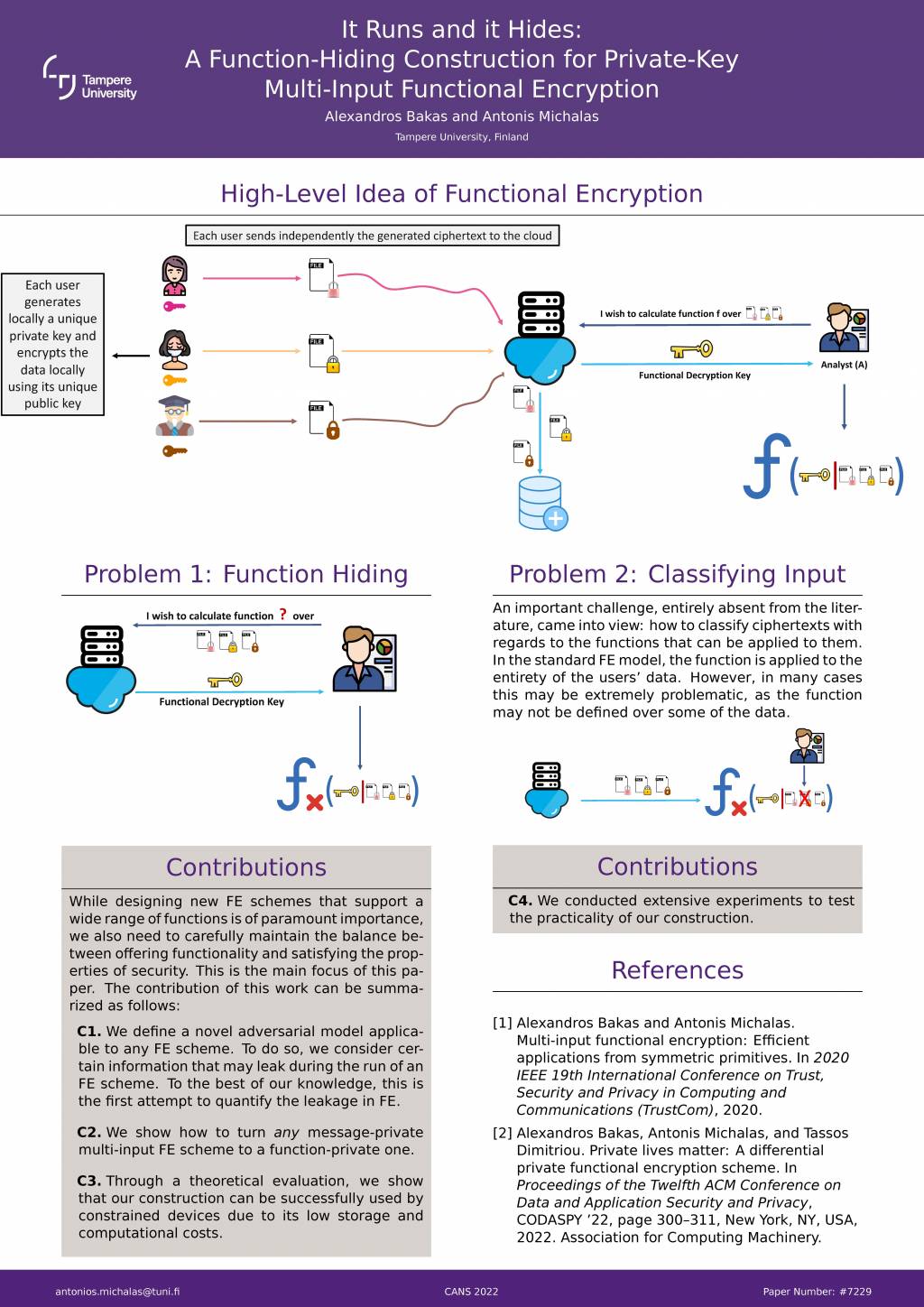
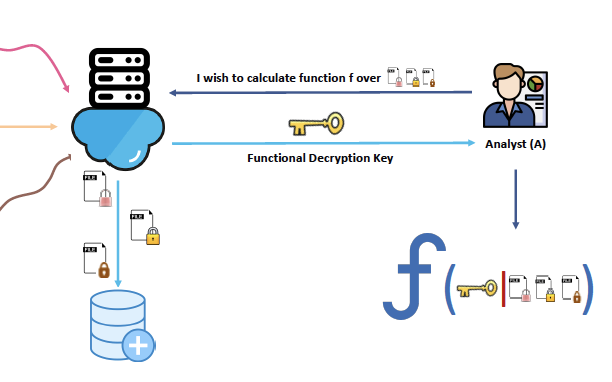
Title: It Runs and it Hides: A Function-Hiding Construction for Private-Key Multi-Input Functional Encryption (accepted as a poster)
Authors: Alexandros Bakas and Antonis Michalas
Venue: Proceedings of the 21st International Conference on Cryptology and Network Security (CANS’22), Abu Dhabi, UAE, November 13–16, 2022.